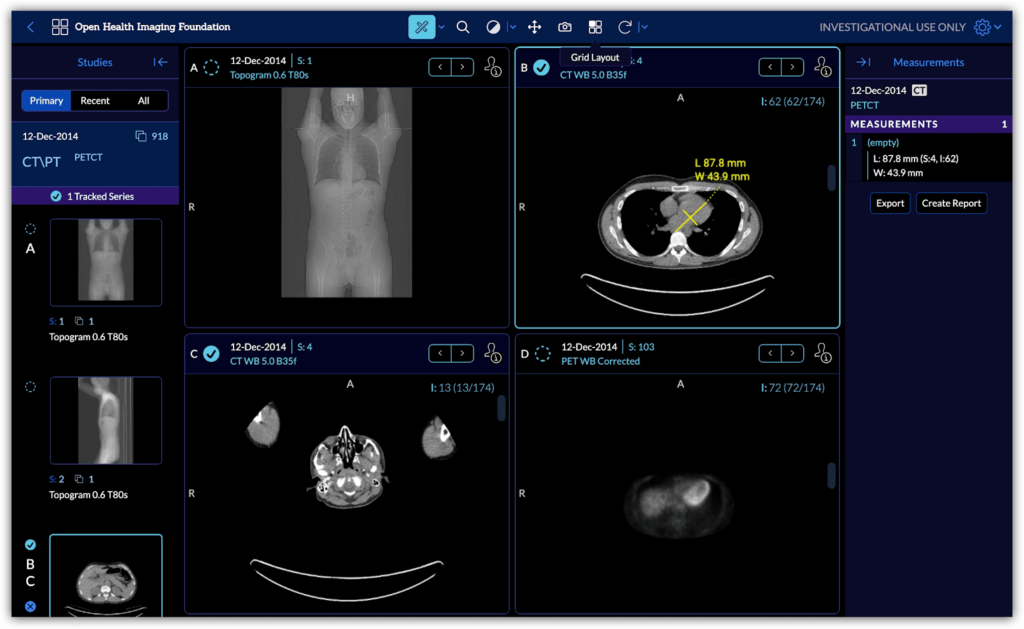
Are you looking for a free DICOM viewer online to view medical images but worried about privacy?
As healthcare organizations adopt web-based viewers for convenience, proper precautions are necessary to protect sensitive patient data.
This guide will discuss privacy risks, securing DICOM traffic, implementing access controls, auditing, and other best practices to keep your DICOM viewers private.
The Privacy Risks of Browser-Based Viewers
Unlike standalone DICOM software secured behind your firewall, web-based viewers introduce new threats:
- Internet transmission creates opportunities for man-in-the-middle attacks to intercept data.
- Browser caches may store images temporarily.
- Cloud servers can introduce new parties and locations for potential data leakage.
- Auditing user access is more challenging in the browser.
Without diligence, patient privacy can be jeopardized.
Securely Transmitting PHI Via TLS/SSL
All traffic containing protected health information (PHI) like medical images requires encryption-in-transit via TLS (Transport Layer Security) or its predecessor SSL (Secure Sockets Layer).
Verify any online DICOM viewer connects using https://, enforcing data encryption between the browser and server.
Encryption protects images as they traverse the internet, preventing prying eyes from accessing data in transit.
Protect Data at rest with Access Controls.
Once data reaches cloud servers, additional access controls can compartmentalize and restrict availability based on user roles:
- Only authorized radiologists, technicians, physicians, specialists, or other staff can access particular studies based on dynamic rules rather than upfront configuration.
- Segment data across multiple cloud accounts or storage mechanisms to limit exposure.
- Before transmitting images externally, mask or exclude sensitive patient identifiers in the DICOM header.
- Automatically purge cached, temporary data after sessions close.
Together, these measures hedge exposure while still enabling availability anytime and anywhere.
Auditing Access
With web-centric viewers, closely monitoring access becomes imperative:
- Log all viewing sessions, including user, date/time, images accessed, client IP address, browser fingerprints, and relevant patient/study metadata.
- Alert on suspicious patterns like users viewing studies irrelevant to their role or unauthorized viewers attempting access.
- Periodically review logs for policy violations and refine rules.
Comprehensive activity trails ensure you can research incidents, tie actions to individuals, hold users accountable, and continually improve protections.
Additional Safeguards
Other techniques further reinforce privacy:
- Integrate multi-factor authentication before granting access to PHI, combining username/password with one-time codes or biometrics for more vigorous identity verification.
- Allow patient-specific consent, empowering individuals to approve or limit data sharing on a study-by-study basis based on their preferences.
- Anonymize studies via DICOM tag modification to remove identifiable health information while preserving imaging data for specific use cases.
- Contractually bind any SaaS platform providers hosting the viewer or related infrastructure to handle data securely in alignment with your policies.
Achieving Both Accessibility and Security
Modern medicine relies on instantly available imaging and interdisciplinary collaboration — but not at the expense of patient confidentiality.
With strong, layered controls, browser-based DICOM viewers can be trustworthy tools, not inherent risks.
Audit logs bring accountability. Encryption prevents tampering. Access rules compartmentalize availability. Together, these precautions help balance accessibility and privacy across the hybrid healthcare landscape.
By taking the proper precautions tailored to your needs, your organization can embrace the convenience of web-based DICOM viewers without compromising your duty to safeguard sensitive patient data.